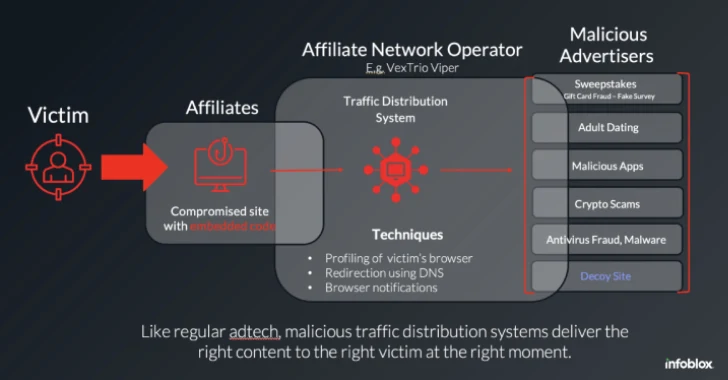
A sprawling web of malicious advertising infrastructure tied to the threat actor group behind VexTrio Viper Traffic Distribution Service (TDS) has been linked to at least two additional traffic distribution operations—Help TDS and Disposable TDS—according to recent threat intelligence research.
These interconnected services form a sophisticated affiliate-driven ecosystem designed to redirect unsuspecting users to malware, scams, phishing sites, and fraudulent offers via compromised websites, smart links, and push notification campaigns.
“VexTrio is not a single service—it’s a criminal adtech consortium composed of multiple interconnected TDSs and affiliate schemes,” researchers noted.
🎯 Core Infrastructure: From Los Pollos to Taco Loco and Beyond
Multiple entities under the VexTrio umbrella include:
- Los Pollos – Recruits malware distributors (publishing affiliates) and monetizes traffic via push notifications
- Taco Loco – Specializes in push monetization
- Adtrafico – Functions as part of the broader affiliate network
These services work by injecting malicious JavaScript into legitimate websites, initiating a redirect chain that leads visitors through traffic broker networks to scam pages or malware payloads. Notable campaigns include Balada Injector, DollyWay, and Sign1, along with DNS TXT record-based redirections—all traced back to the VexTrio ecosystem.
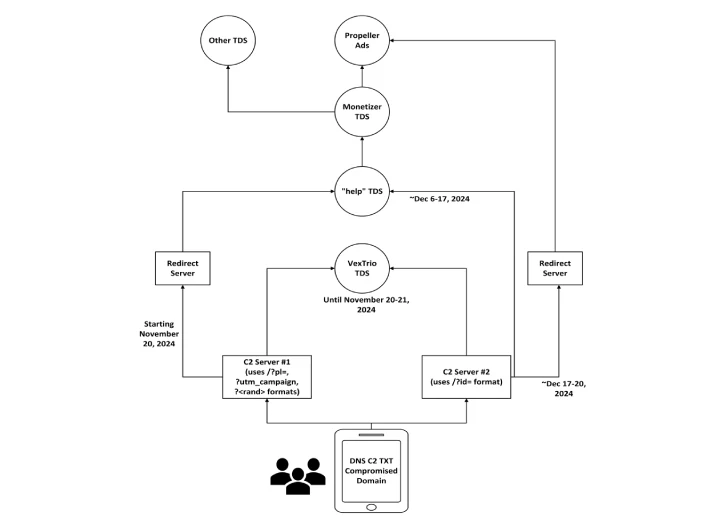
🌐 DNS TXT Campaigns and the Rise of Help TDS
An extensive DNS telemetry analysis of 4.5 million TXT records revealed that the redirect infrastructure could be split into two distinct C2 clusters—both tied to Russian-hosted infrastructure, each maintaining separate domains and behaviors.
While initially pointing to VexTrio, both clusters have since rerouted traffic through Help TDS, which has now shifted its redirection endpoint to a monetization platform called Monetizer.
- Help TDS and Disposable TDS appear to be operationally unified, enjoying an “exclusive relationship” with VexTrio prior to November 2024
- Post-research exposure, services like Los Pollos ceased push-link operations, leading to a migration toward Help TDS
Despite having fewer features than VexTrio’s main platform, Help TDS retains Russian infrastructure and continues to share software elements, suggesting close coordination or shared development lineage.
“The movement from VexTrio to Help TDS may appear like diversification, but the backend relationships suggest a tightly-knit operation rather than a true shift,” experts concluded.
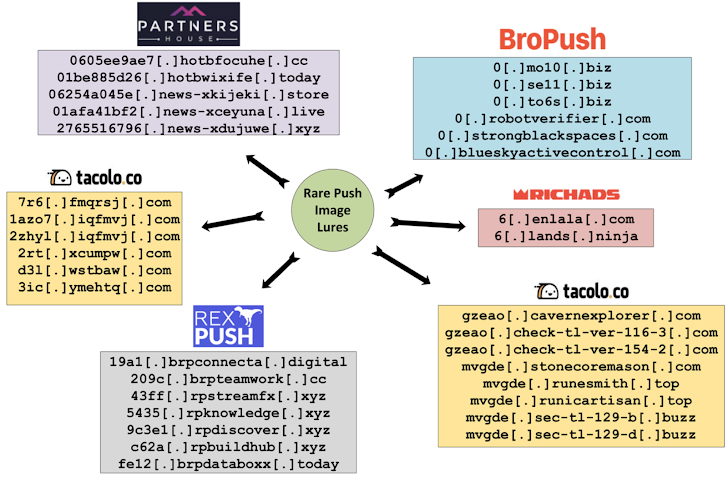
🚨 TDS-as-a-Service and Commercial AdTech Abuse
VexTrio is one among several traffic distribution services masquerading as advertising platforms. Others include:
- Partners House
- BroPush
- RichAds
- Admeking
- RexPush
These platforms increasingly exploit Google Firebase Cloud Messaging (FCM) and Push API-based scripts to deliver malicious content via push notifications, often disguised as browser alerts or fake updates.
Year after year, hundreds of thousands of compromised WordPress and CMS-based websites are used as entry points into this network.
🔍 Accountability Gap and Affiliate Vetting Loopholes
While many of these TDSs operate as registered commercial entities, including in jurisdictions with Know Your Customer (KYC) requirements, little is done to enforce user or affiliate transparency.
“VexTrio and its affiliate programs have sufficient insight to identify their malware-distributing partners—but enforcement remains absent, allowing the system to flourish,” threat analysts warned.
📌 SecurityX Insight
The rise of multi-layered traffic distribution systems like VexTrio reflects the blurring lines between cybercrime and commercial adtech. These TDS networks facilitate malware distribution at scale while hiding behind legitimate-looking business models, leveraging compromised infrastructure and cloud-based delivery methods to stay under the radar.
Organizations should:
- Regularly audit web environments for unauthorized JavaScript injections
- Monitor outbound DNS TXT queries and unusual redirect chains
- Implement content security policies (CSP) and domain whitelisting
- Educate users on browser-based push notification risks


Leave a Reply