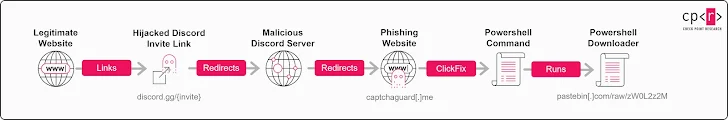
A newly uncovered malware campaign has demonstrated how threat actors are abusing Discord’s vanity invite system to silently redirect users to malicious servers, ultimately delivering AsyncRAT and a customized Skuld information stealer.
At the core of the campaign is a flaw in Discord’s invite mechanism that allows attackers to reuse expired or deleted invite codes when creating custom vanity links. This makes it possible for a previously legitimate Discord invite link—shared publicly on forums, blogs, or social media—to be silently hijacked and redirected to a malicious server controlled by threat actors.
🎯 Attack Flow: From Trusted Invite to Full Compromise
Once users click on the hijacked link and join the rogue server, they’re prompted to complete a “verification” process. This step uses the ClickFix social engineering tactic to manipulate users into executing a malicious PowerShell command on their own systems.
Breakdown of the infection chain:
- User joins a Discord server via a hijacked invite link
- A fake bot prompts them to click a “Verify” button
- Behind the button:
- A hidden script copies a PowerShell command to the clipboard
- The user is instructed to paste and run the “verification string”
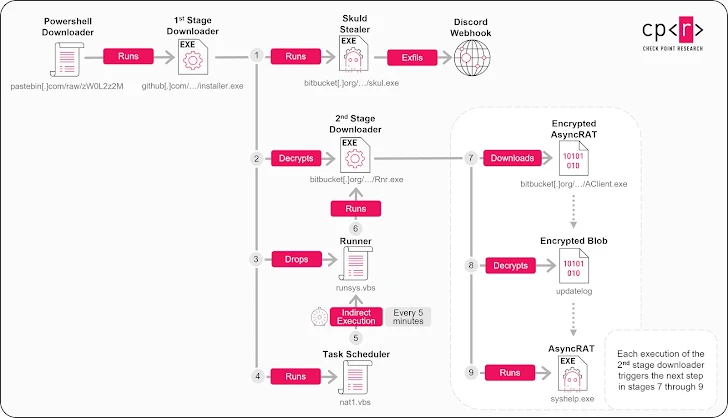
- This initiates a multi-stage payload download via Pastebin and Bitbucket
- Final payloads dropped:
- AsyncRAT – a remote access trojan capable of full system control
- Skuld Stealer – a Golang-based malware targeting Discord data, crypto wallets, and gaming platforms
The malware employs sandbox evasion, Unicode obfuscation, and cloud-based hosting to bypass traditional security tools. The delivery chain is hosted on trusted services like GitHub, Pastebin, Bitbucket, and Discord itself, allowing attackers to blend in with legitimate traffic.
💰 Targeting Crypto Wallets and Digital Assets
The customized Skuld Stealer demonstrates a clear financial motivation. It is equipped to:
- Extract wallet seed phrases and passwords from Exodus and Atomic crypto wallets
- Replace legitimate application files using a technique known as wallet injection
- Bypass Chrome’s app-bound encryption with a tool derived from ChromeKatz
- Exfiltrate collected data through Discord webhooks
These techniques allow the attacker to gain direct access to cryptocurrency funds, credentials, and sensitive user data without triggering alerts.
⚙️ Related Campaign: Malware Masquerading as Game Crack Tools
In a parallel campaign attributed to the same threat actor, the loader was repackaged as a cracked game utility and distributed via Bitbucket. This version has already been downloaded over 350 times, suggesting ongoing activity.
Victims of both campaigns are primarily located in the United States, Vietnam, France, Germany, Slovakia, Austria, the Netherlands, and the United Kingdom.
🔒 Mitigation and Response
- Discord has since disabled the malicious bot infrastructure, breaking the ongoing infection chain.
- Users and community admins should treat expired or inactive invite links with caution and avoid relying on vanity URLs without validation.
- Organizations should monitor for signs of PowerShell misuse, network connections to Pastebin or Bitbucket, and suspicious clipboard or Run dialog activity.
- Developers should avoid using third-party tools or cracks from untrusted sources, especially those hosted on public repositories.
📌 SecurityX Insight:
This campaign underscores how subtle features in popular platforms like Discord can be turned into high-impact attack vectors. By hijacking the trust embedded in shared invite links, attackers can bypass traditional phishing filters and lure users into self-infection via clever social engineering. The targeting of cryptocurrency wallets and use of trusted infrastructure for delivery highlights a rising trend in stealthy, profit-driven malware campaigns.



Leave a Reply