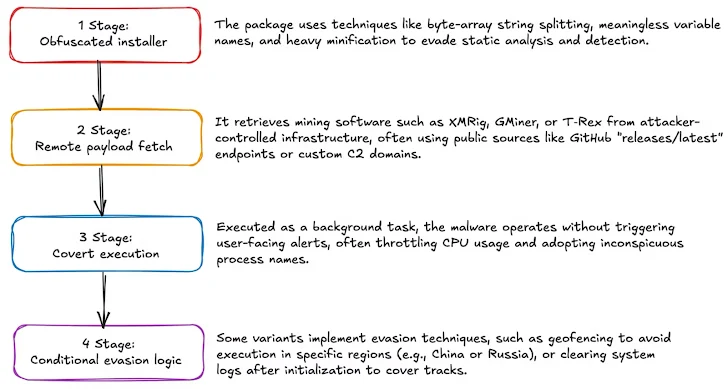
Recent discoveries have exposed a growing wave of malware-laden open-source packages infiltrating popular repositories such as npm and PyPI, highlighting the increasing sophistication and stealth of supply chain attacks targeting developers, infrastructure, and cryptocurrency assets.
🛠️ Malicious npm Packages Conceal Multi-Stage Remote Access Tools
Researchers identified several malicious npm packages, which were quickly removed after being downloaded hundreds of times:
eslint-config-airbnb-compat(676 downloads)ts-runtime-compat-check(1,588 downloads)solders(983 downloads)@mediawave/lib(386 downloads)
These packages were designed to execute remote code, retrieve payloads from external servers, and in some cases, install persistent remote access tools.
One example used a transitive dependency chain: eslint-config-airbnb-compat depended on ts-runtime-compat-check, which contacted a remote server (proxy.eslint-proxy[.]site) to retrieve and run Base64-encoded payloads—effectively concealing its true behavior several layers deep.
Another package, solders, included a postinstall script that triggered malicious code on installation. Through Unicode-based obfuscation, the malware disguised itself as a string of Japanese characters, ultimately revealing logic that:
- Detected Windows environments
- Fetched second-stage payloads via PowerShell from remote hosts
- Added Windows Defender exclusions
- Executed a .NET-based Remote Access Trojan (Pulsar RAT) hidden within a PNG image hosted on a public image-sharing site
The malware went as far as manipulating Windows Task Scheduler, bypassing User Account Control (UAC), and injecting secondary .NET payloads into memory—demonstrating exceptional layering and intent to evade detection.
💸 Threats Targeting Cryptocurrency Developers and Wallets
Alongside the npm campaign, security analysts uncovered numerous crypto-focused malicious packages designed to compromise wallets and steal funds, including:
express-dompurifyandpumptoolforvolumeandcomment– steal browser credentials and wallet keysbs58js– drains crypto wallets and uses multi-hop transfers to obscure traceslsjglsjdv,asyncaiosignal,raydium-sdk-liquidity-init– function as clippers, replacing copied wallet addresses in the clipboard with attacker-controlled destinations
These packages illustrate an increasingly tailored threat landscape targeting Web3 and blockchain developers, with high-value thefts and advanced obfuscation techniques becoming common.
🤖 AI-Assisted Coding Introduces Slopsquatting Risks
As AI coding assistants gain traction, a novel vector—slopsquatting—has emerged. In this scenario, AI-generated code hallucinates plausible but non-existent package names. If attackers anticipate and pre-register those names, they can deliver malicious payloads to unsuspecting developers.
In one example, a hallucinated package starlette-reverse-proxy crashed a build process due to non-existence. Had a threat actor uploaded a fake version, the attack could have succeeded silently.
While advanced agents and frameworks (e.g., Codex CLI, Claude Code CLI, Cursor AI with MCP validation) help reduce this risk, phantom package hallucination remains a gap even in modern workflows.
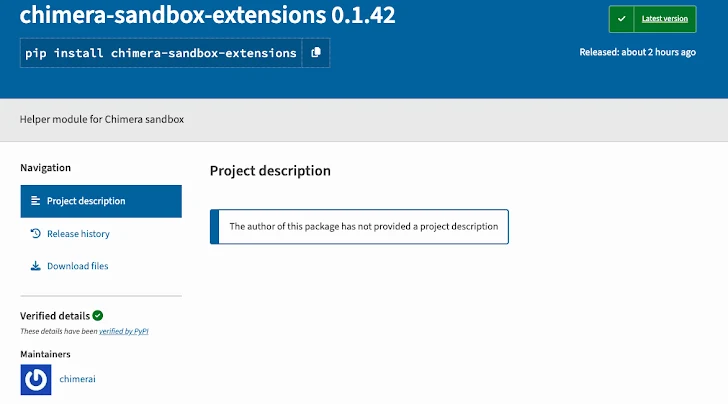
🧪 Red Team Simulation or Misinterpreted Malware? The chimera-sandbox-extensions Case
One particularly sophisticated package, chimera-sandbox-extensions, appeared on PyPI with credential-stealing functionality—including exfiltration of:
- AWS tokens and CI/CD secrets
- macOS Jamf receipts
- Git configuration and Zscaler settings
- Public IP and host metadata
The malware contacted an attacker-controlled domain (generated via domain generation algorithm) to retrieve a second-stage Python payload and assess targets for further exploitation.
However, it was later revealed that the package had been uploaded as part of an authorized red teaming simulation by a major tech firm to test internal defenses. The simulation did not execute on external systems, but its realism underscores the blurred lines between legitimate offensive security and malicious campaigns in public ecosystems.
📌 SecurityX Insight
The convergence of open-source development, AI-generated code, and targeted financial incentives is widening the attack surface of the software supply chain. Recent findings underscore several key risks:
- Deeply obfuscated multi-stage loaders that evade standard defenses
- Clipboard-hijacking clippers and wallet drainers targeting crypto ecosystems
- Phantom packages introduced through AI-assisted hallucination
- Red team tools indistinguishable from real malware in public repositories
Organizations and developers must treat public package registries with increased caution:
- Enforce strict dependency validation
- Monitor for unexpected installation behaviors
- Use sandbox testing for unverified packages
- Adopt SBOM (Software Bill of Materials) tracking and runtime behavioral monitoring



Leave a Reply