A newly documented cyber-espionage campaign has revealed how the state-sponsored group APT41 leveraged Google Calendar as a covert channel for command-and-control (C2) communications in its latest attacks targeting government entities.
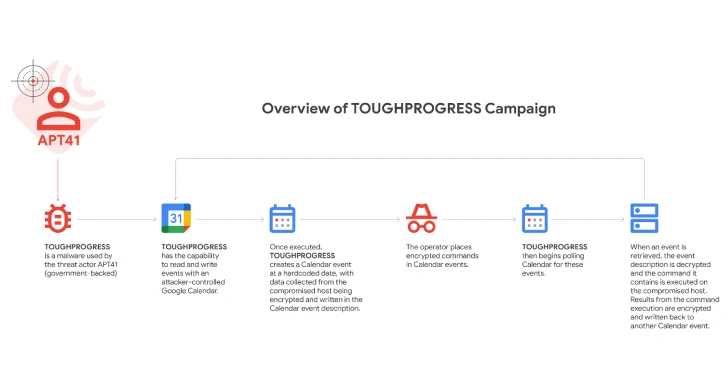
Discovered in late October 2024, the operation involved a custom malware strain known as TOUGHPROGRESS, which was found hosted on a compromised government website. The infrastructure was used to send targeted spear-phishing emails to other government organizations, embedding weaponized ZIP archives that initiate infection via disguised Windows shortcut files (LNK).
The ZIP archives typically contained a folder filled with decoy image files and a malicious shortcut impersonating a PDF. Once launched, the malware began a multi-stage execution chain aimed at silently deploying TOUGHPROGRESS on the victim system.
🧬 Infection Chain and Technical Breakdown
The attack was composed of three payload stages, each with a distinct purpose:
- PLUSDROP – A DLL file that decrypts and executes the next stage entirely in memory.
- PLUSINJECT – Performs process hollowing on a legitimate
svchost.exeto inject the core payload. - TOUGHPROGRESS – The final malware stage, responsible for establishing C2 via Google Calendar.
TOUGHPROGRESS communicates with attacker-controlled Calendar events, using them to receive commands and exfiltrate stolen data. Specifically, the malware:
- Creates zero-duration events at hardcoded timestamps (e.g., May 30, 2023).
- Writes encrypted output data into event descriptions.
- Retrieves and decrypts instructions embedded in Calendar events dated July 30–31, 2023.
This use of a legitimate cloud service allows the malware to bypass traditional detection mechanisms, blending in with normal traffic patterns and evading network-level security controls.
🕵️ Threat Actor Profile: APT41
APT41 is a well-documented Chinese nation-state group, known under various aliases including Winnti, HOODOO, Brass Typhoon, and Wicked Panda. It has a long track record of campaigns targeting industries such as:
- Government and defense
- Shipping and logistics
- Technology and media
- Manufacturing and energy
In recent years, the group has carried out operations in Italy, Taiwan, the U.K., Spain, and Thailand, and continues to evolve its tools and delivery methods.
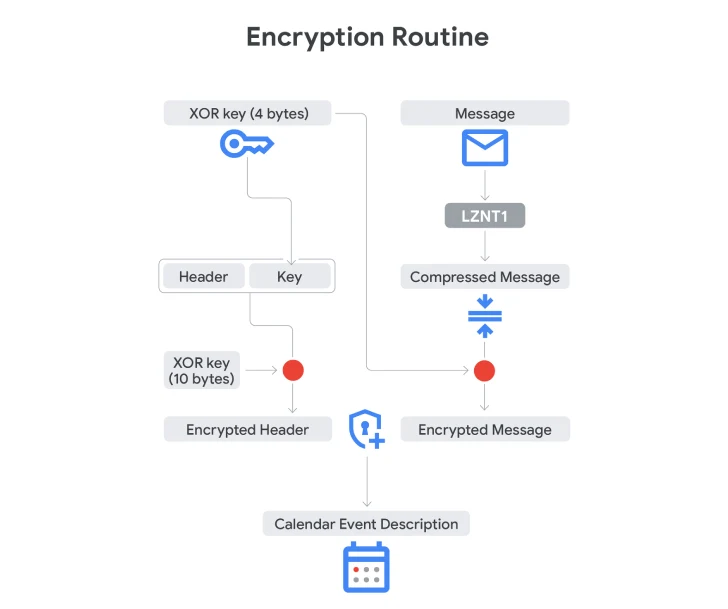
The newly exposed campaign follows previous activity where APT41 used Google Drive to deliver backdoors such as GC2 (Google Command and Control) and relied on Google Sheets for real-time command execution.
✅ Mitigation and Response
According to reports, the cloud-based infrastructure—including the malicious Google Calendar instance and associated Google Workspace projects—has since been taken offline, effectively disrupting the operation. Affected organizations were notified, although the full scale of the campaign remains unknown.
The misuse of mainstream cloud platforms—especially for stealthy C2—represents a growing challenge for defenders, as it complicates detection and response by masking malicious behavior within trusted services.
📌 SecurityX Insight:
This incident underscores the increasing abuse of cloud collaboration platforms by advanced threat actors. Defenders should expand their threat models to include non-traditional C2 channels, implement behavioral monitoring for cloud app usage, and apply zero-trust principles to both endpoint and cloud environments.



Leave a Reply